Experts discovered that Operation Triangulation targeting Apple iOS devices leveraged an undocumented hardware feature.
Researchers from the Russian cybersecurity firm Kaspersky discovered that threat actors behind the Operation Triangulation exploited an undocumented hardware feature to target Apple iOS devices.
In early June, Kaspersky uncovered a previously unknown APT group that is targeting iOS devices with zero-click exploits as part of a long-running campaign dubbed Operation Triangulation.
The experts discovered the attack while monitoring the network traffic of their own corporate Wi-Fi network dedicated to mobile devices using the Kaspersky Unified Monitoring and Analysis Platform (KUMA).
According to Kaspersky researchers, Operation Triangulation began at least in 2019 and is still ongoing.
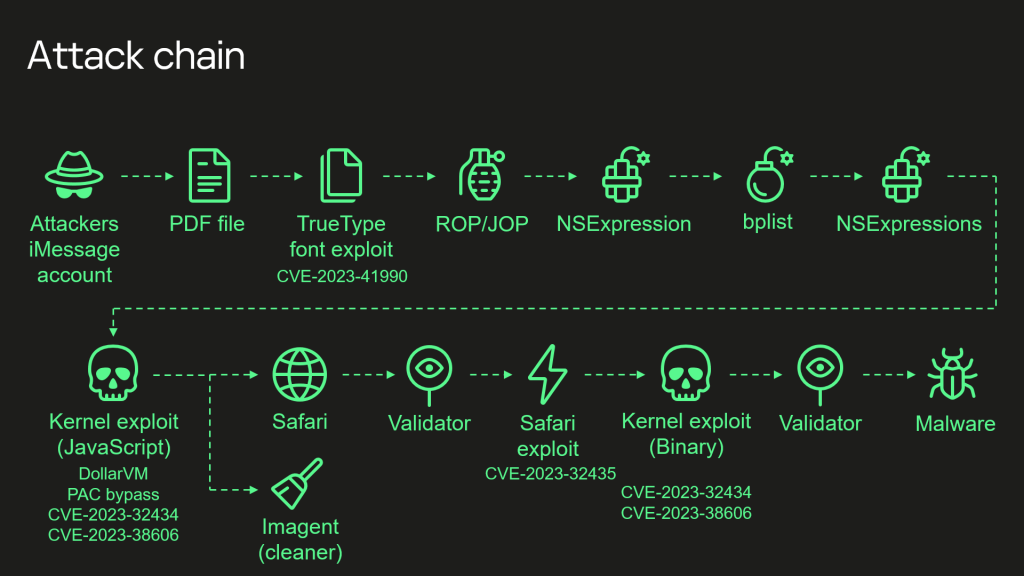
The attack chains commenced with a message sent via the iMessage service to an iOS device. The message has an attachment containing an exploit. The expert explained that the message triggers a remote code execution vulnerability without any user interaction (zero-click).
Shortly after Kaspersky’s disclosure, Russia’s FSB accused the US intelligence for the attacks against the iPhones. According to Russian intelligence, thousands of iOS devices belonging to domestic subscribers and diplomatic missions and embassies have been targeted as part of Operation Triangulation.
The operations aimed at gathering intelligence from diplomats from NATO countries, Israel, China and Syria.
FSB believes that Apple supported US intelligence in this cyberespionage campaign.
Kaspersky initially reported that the exploit used in the attack downloads multiple subsequent stages from the C2 server, including additional exploits for privilege escalation. The final payload is downloaded from the same C2 and is described by Kaspersky as a fully-featured APT platform.
Then the initial message and the exploit in the attachment are deleted.
The researchers noticed that the malicious toolset does not support persistence, likely due to the limitations of the OS. The devices may have been reinfected after rebooting.
The attack successfully targeted iOS 15.7, the analysis of the final payload has yet to be finished. The malicious code runs with root privileges, it supports a set of commands for collecting system and user information, and can run arbitrary code downloaded as plugin modules from the C2 server.
In June, Kaspersky that after a six-month-long investigation, they completed the collection of all the components of the attack chain and the analysis of the spyware implant, tracked as TriangleDB.
The attackers exploit the implant kernel vulnerability to obtain root privileges on the target iOS device and install the implant. The spyware is directly deployed in memory, but if the victim reboots the device the malware doesn’t persist. In any case, the implant uninstalls itself after 30 days if the system is not rebooted. However, attackers can extend this period.
On December 27, 2023, delivered a presentation, titled, “Operation Triangulation: What You Get When Attack iPhones of Researchers”, at the 37th Chaos Communication Congress (37C3), held Hamburg. The researchers presented the results of their investigation into Operation Triangulation conducted with their colleagues,
The researchers explained that recent iPhone models support additional hardware-based security protection for sensitive areas of the kernel memory. The security feature protection prevents attackers from taking over the device by controlling the kernel memory by exploiting the flaw CVE-2023-32434. Kaspersky discovered that to bypass this hardware-based security protection, threat actors abused a hardware feature of Apple-designed SoCs.
“Our guess is that this unknown hardware feature was most likely intended to be used for debugging or testing purposes by Apple engineers or the factory, or that it was included by mistake. Because this feature is not used by the firmware, we have no idea how attackers would know how to use it” continues the experts.
Numerous peripheral devices within the SoC relies dedicated hardware registers for CPU operations. These registers are linked to CPU-accessible memory (“memory-mapped I/O (MMIO)).”
The experts pointed out that address ranges for MMIOs of peripheral devices in Apple products (including iPhones, Macs, and others) are stored in a specific file format called DeviceTree.
The analysis of the exploit used in the Operation Triangulation attack revealed that most of the MMIOs used by the threat actors do not belong to any MMIO ranges defined in the device tree. The exploit specifically targets Apple A12–A16 Bionic SoCs, targeting unknown MMIO blocks of registers.
“This is no ordinary vulnerability, and we have many unanswered questions. We do not know how the attackers learned to use this unknown hardware feature or what its original purpose was. Neither do we know if it was developed by Apple or it’s a third-party component like ARM CoreSight.” concludes the report. “What we do know—and what this vulnerability demonstrates—is that advanced hardware-based protections are useless in the face of a sophisticated attacker as long as there are hardware features that can bypass those protections. Pierluigi Paganini
(SecurityAffairs – hacking, German hospital network)
- Triangulation in General Contexts:
- Triangulation Method: In research or survey methodologies, triangulation involves using multiple sources or methods to validate or cross-verify data, aiming for more accurate results.
- Location Triangulation: In geographic or GPS contexts, triangulation involves determining a location by intersecting signals from multiple sources or satellites.
- Protecting Against Cyber Threats (General Tips): Even though there might not be specific information available on an “Operation Triangulation” attack, users can take these general cybersecurity precautions to protect themselves:
- Stay Informed: Keep up-to-date with the latest news on cybersecurity threats and attacks. Subscribe to reputable cybersecurity blogs or newsletters to stay informed.
- Use Strong Authentication: Enable two-factor authentication (2FA) whenever possible for your online accounts.
- Regularly Update Software: Keep your operating systems, applications, and antivirus/anti-malware software updated to patch known vulnerabilities.
- Be Cautious of Phishing: Be vigilant against phishing attempts. Avoid clicking on suspicious links or providing personal information to unknown sources.
- Secure Passwords: Use strong, unique passwords for different accounts. Consider using a reliable password manager to generate and store complex passwords securely.
- Backup Data: Regularly back up important data to a secure, offline location to mitigate the impact of potential ransomware attacks or data loss.
- Use a Firewall: Enable and configure firewalls on your devices to monitor and block unauthorized access attempts.
- Educate Yourself: Understand common cybersecurity threats and best practices. Many cybersecurity organizations offer free resources and tips for users.
Given the evolving nature of cyber threats, it’s essential to stay vigilant and adopt best practices to protect yourself against potential attacks, even if the specific details of an “Operation Triangulation” attack are not widely known or defined within cybersecurity discourse as of my last update. Regularly updating your cybersecurity knowledge and implementing strong security measures can significantly reduce the risk of falling victim to various cyber threats.